DHS/FBI Alert: Russian Government Cyber Activity Targeting Power Grid
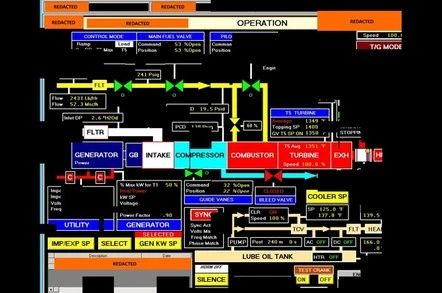
In an unprecedented alert, the US Department of Homeland Security (DHS) and FBI have warned of persistent attacks by Russian government hackers on critical US government sectors, including energy, nuclear, commercial facilities, water, aviation and manufacturing.
The alert details numerous attempts extending back to March 2016 when Russian cyber operatives targeted US government and infrastructure.
The DHS and FBI said: “DHS and FBI characterise this activity as a multi-stage intrusion campaign by Russian government cyber-actors who targeted small commercial facilities’ networks, where they staged malware, conducted spear phishing and gained remote access into energy sector networks.
What follows is an excerpt from the DHS/FBI Alert:
- Systems Affected
- Domain Controllers
- File Servers
- Email Servers
- Overview
This joint Technical Alert (TA) is the result of analytic efforts between the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI). This alert provides information on Russian government actions targeting U.S. Government entities as well as organizations in the energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors. It also contains indicators of compromise (IOCs) and technical details on the tactics, techniques, and procedures (TTPs) used by Russian government cyber actors on compromised victim networks. DHS and FBI produced this alert to educate network defenders to enhance their ability to identify and reduce exposure to malicious activity.
DHS and FBI characterize this activity as a multi-stage intrusion campaign by Russian government cyber actors who targeted small commercial facilities’ networks where they staged malware, conducted spear phishing, and gained remote access into energy sector networks. After obtaining access, the Russian government cyber actors conducted network reconnaissance, moved laterally, and collected information pertaining to Industrial Control Systems (ICS).
Read the Complete Article Here:
http://online.electricity-today.com/electricity-today/spring-2018/~14/









